Let us evaluate your secure hardware needs
Let us craft a custom security solution blending hardware and software that fits perfectly with your existing systems. We assess each practice individually, using tailored criteria, and offer scalable solutions that fit practices of any size.
We take an ITIL inspired approach to security
At Hiypa, we follow a systematic, ITIL-inspired approach to developing a unique security solution for each medical practice.
This ensures that every aspect of your security is meticulously considered and tailored to your specific needs. Our process not only covers all critical areas but also generates a comprehensive set of auditable configuration documents.

Assessment of IT Needs
Our first step in creating a tailored security solution is to map out your practice’s IT needs, starting with your Electronic Records Management (ERM) system. By focusing on this critical component, we ensure that all security measures are aligned with how your practice manages patient data. From there, we work backward, identifying and securing each connected system and process.
Linux Applications
At the heart of our security solutions is a robust Linux foundation, with Qubes OS serving as the core system. For most tasks, we utilize Fedora as the default environment, offering a reliable and familiar interface that’s broadly compatible with the majority of healthcare software requirements.
Windows Applications
To accommodate Windows-specific software solutions, we deploy virtualized Windows machines within our system. These virtual machines are run as isolated containers, ensuring that each application operates securely, independent of the others.
Virtualized Desktops
Our system is fully compatible with the majority of virtualized desktop solutions available today. By running these desktops within isolated containers, we ensure that each environment remains secure and independent, providing advanced data protection.

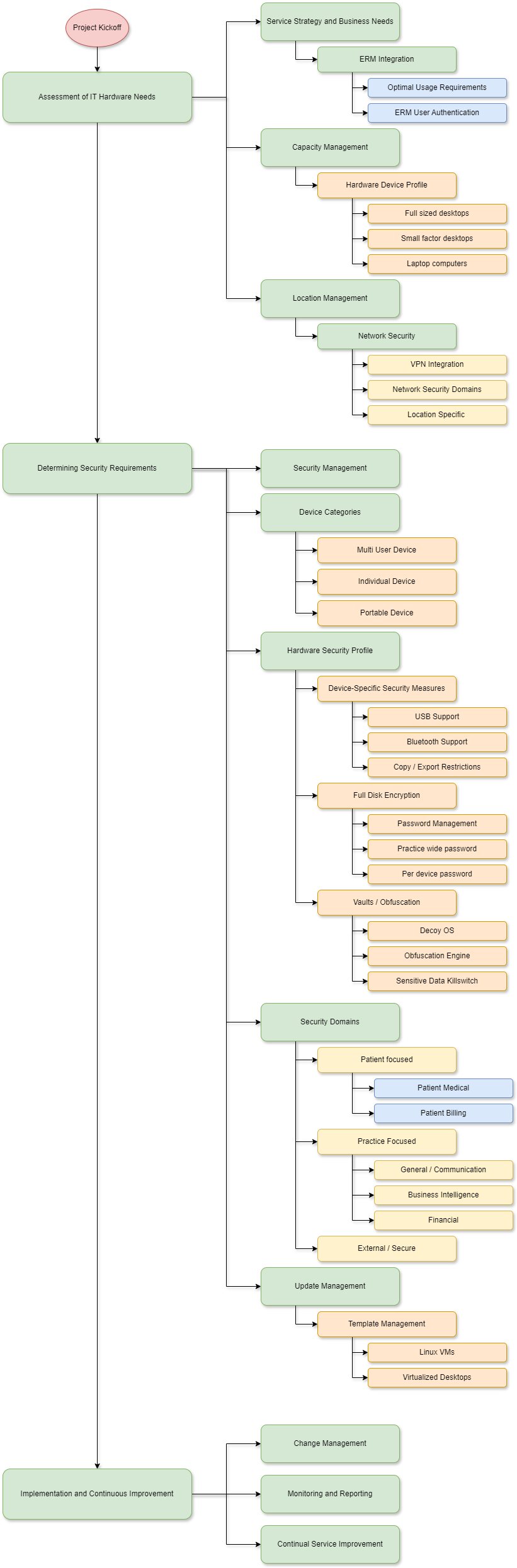
Develop a unique profile for your practice
We assess the number and type of devices required for your practice. This includes everything from desktops and laptops to specialized medical equipment, all tailored to your practice’s unique demands.
Next, we evaluate the medical records systems you use and the network security parameters in place.
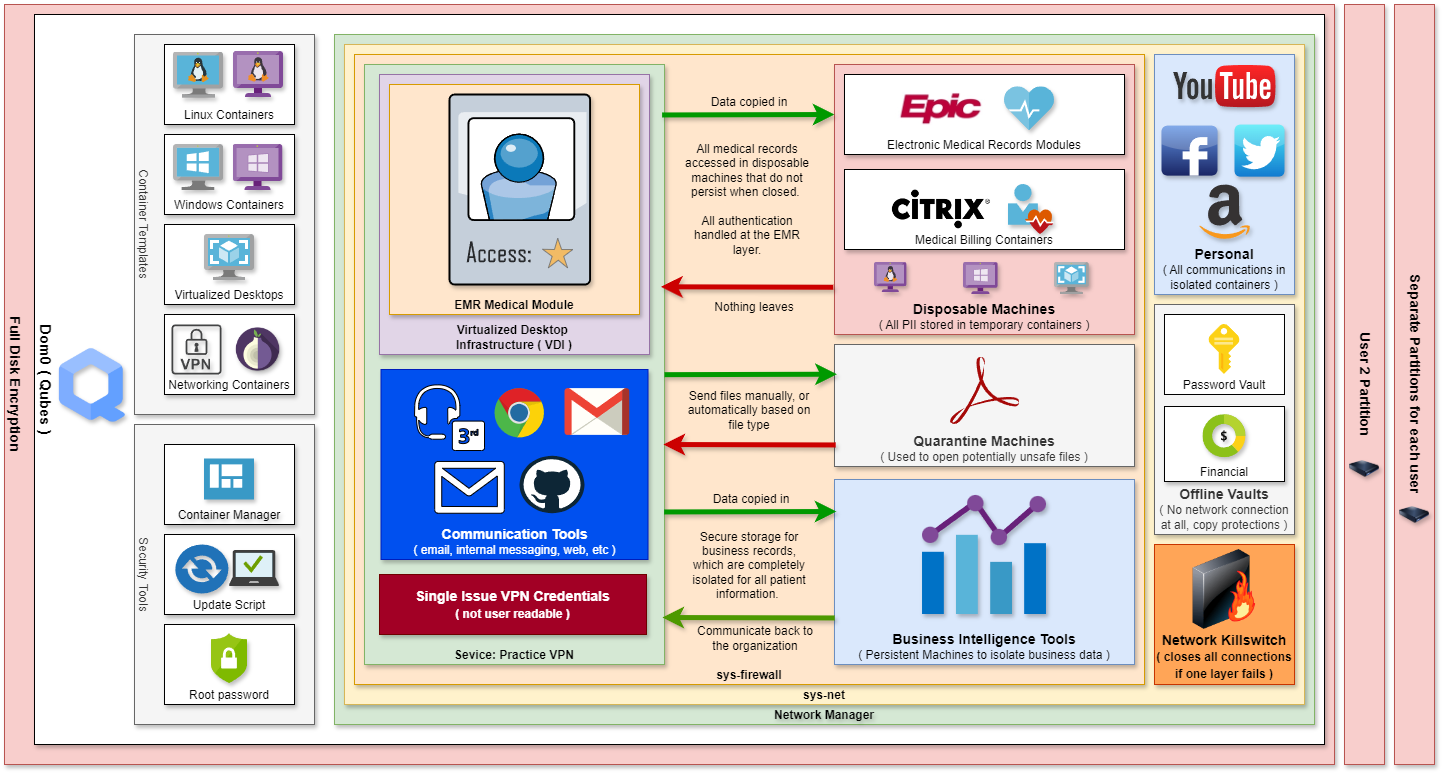
Hardware Security Profiles
We develop specific security profiles tailored to your practice’s needs. This includes creating templates for the isolated containers that will house your applications, ensuring each container is optimized for security and performance.
We also design configuration scripts customized for your environment, allowing for seamless integration and enhanced protection.
Our security profiles include advanced options such as full disk encryption to safeguard sensitive data, obfuscation techniques to hide critical information, and the use of decoy files and operating systems .
Isolated Containers
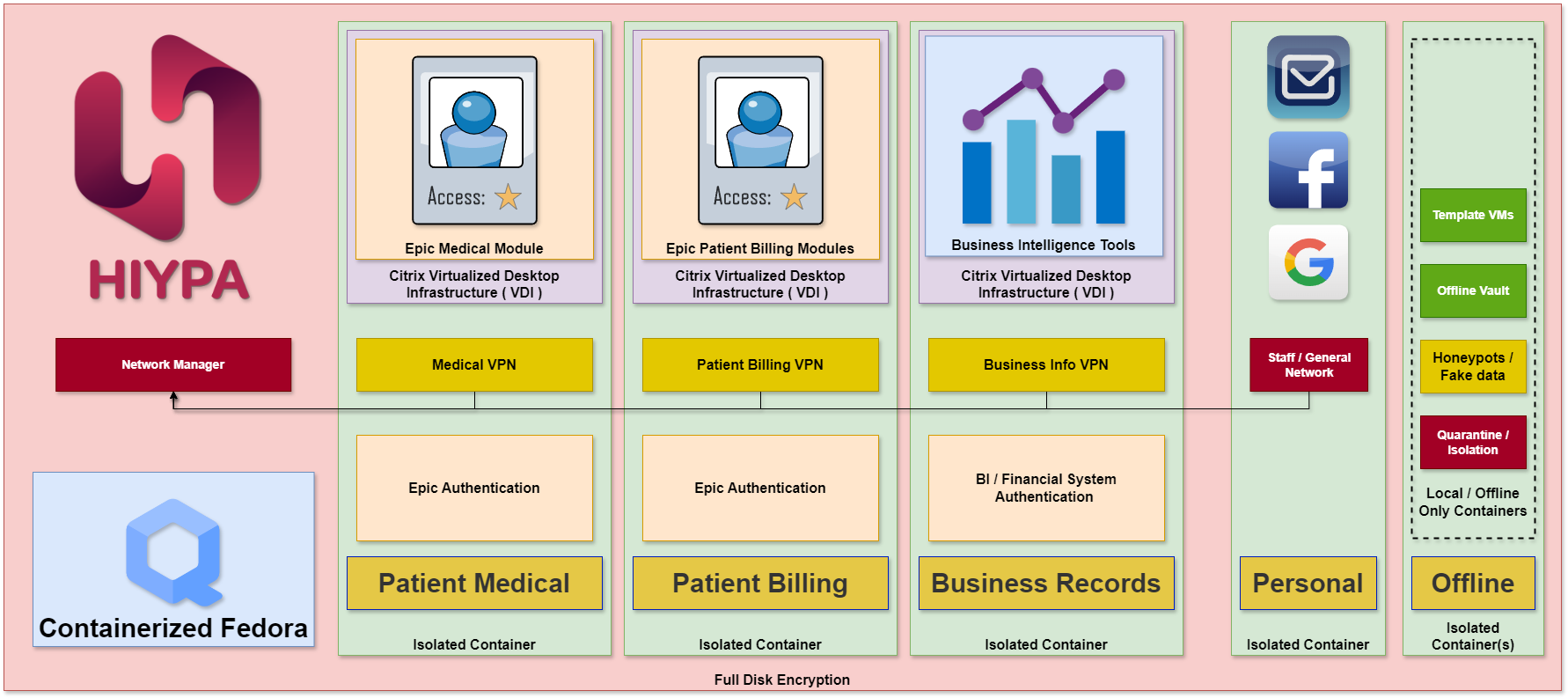
We implement security domains within our system, segmenting different types of data into isolated containers that operate independently from one another.
These containers are designed so they cannot see or interact with each other, creating a strict boundary that ensures data remains secure within its designated domain.
Document ERM Requiernments
Our process begins with a detailed documentation of your Electronic Records Management (ERM) system’s specific needs.
From this starting point, we work backward, designing a uniquely secure environment that integrates seamlessly with your existing infrastructure.
Establish Security Domains
We establish specific security domains to keep your practice’s data isolated and secure. For patient medical data, we create a dedicated security domain that ensures only authorized devices and personnel can access this sensitive information.
Similarly, we set up a separate security domain for billing data, allowing for granular control over which devices can interact with financial records.
This separation ensures that patient information and billing data are never mixed, reducing the risk of unauthorized access and maintaining compliance with industry regulations.
In addition to patient and billing data, we also create security domains to protect your practice’s operational data, including financial records and other critical business information.
To further enhance security, we implement a communication domain that keeps all your practice’s messaging and correspondence separate from other data.
Each application and function operates in its own secure domain, making it impossible for malware or unauthorized access to breach patient data across containers.
Configure Device Security
Next, we create granular security profiles tailored for each device in your practice. These profiles start with isolated user partitions that feature full disk encryption, ensuring that each user’s data is securely stored and protected.
Within this environment, each security domain runs inside its own isolated container, keeping information strictly segmented so it cannot be accessed by any other layer.
To further enhance security, we implement specific copy/paste controls that govern where information can be transferred. For instance, while you can copy information into the patient data domains, extracting data out of these domains is restricted, ensuring that sensitive information remains secure and contained.
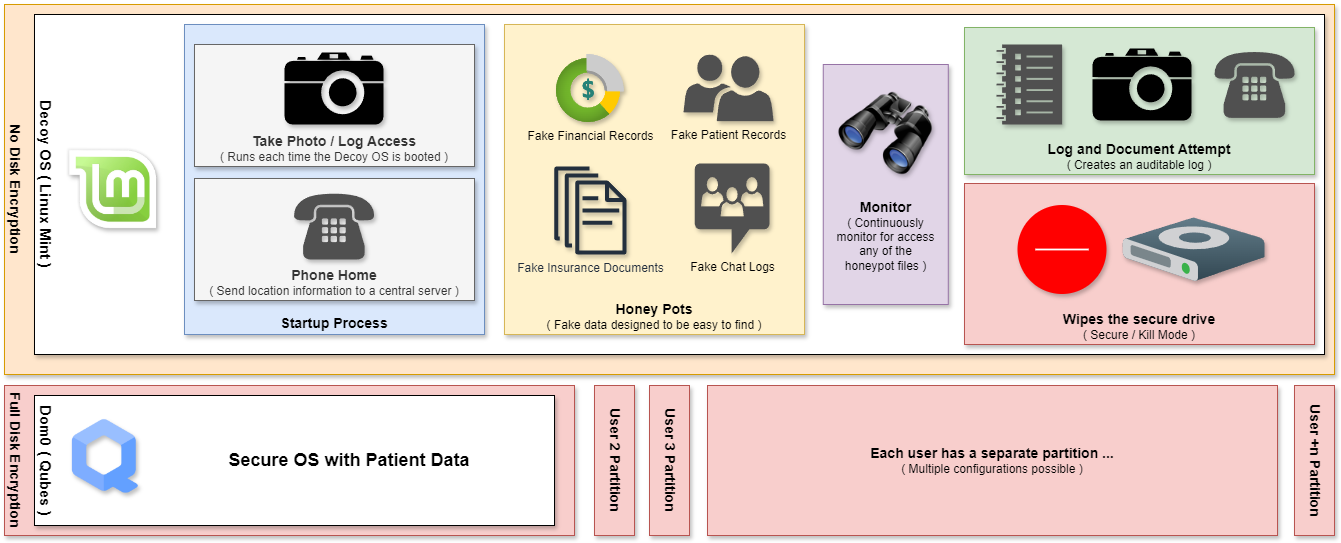
Advanced Obfuscation Engine and Killswitch
We add an extra layer of security with a decoy operating system, specifically designed to be easy to access if a device is compromised. Once this decoy OS is entered, the device will immediately “phone home” to the central server, triggering a discreet alert and capturing a photo of the person accessing the machine.
Additionally, we deploy honeypots—caches of fake files that entice attackers. If an intruder attempts to access these honeypots, it will quietly initiate a process that securely deletes any sensitive information on the device, protecting your practice’s data even in the event of a breach.

Customizable Hardware to Fit Your Practice’s Needs
Our technology is highly flexible, allowing our software to operate efficiently on most hardware configurations. This enables us to utilize the most cost-effective options, whether you require standard-sized desktops, small form “micro devices,” or full-sized high-end desktops.

Standard desktops

"Micro" desktops